Fun Tips About How To Detect Arp Spoofing
Here, you will be able to find.
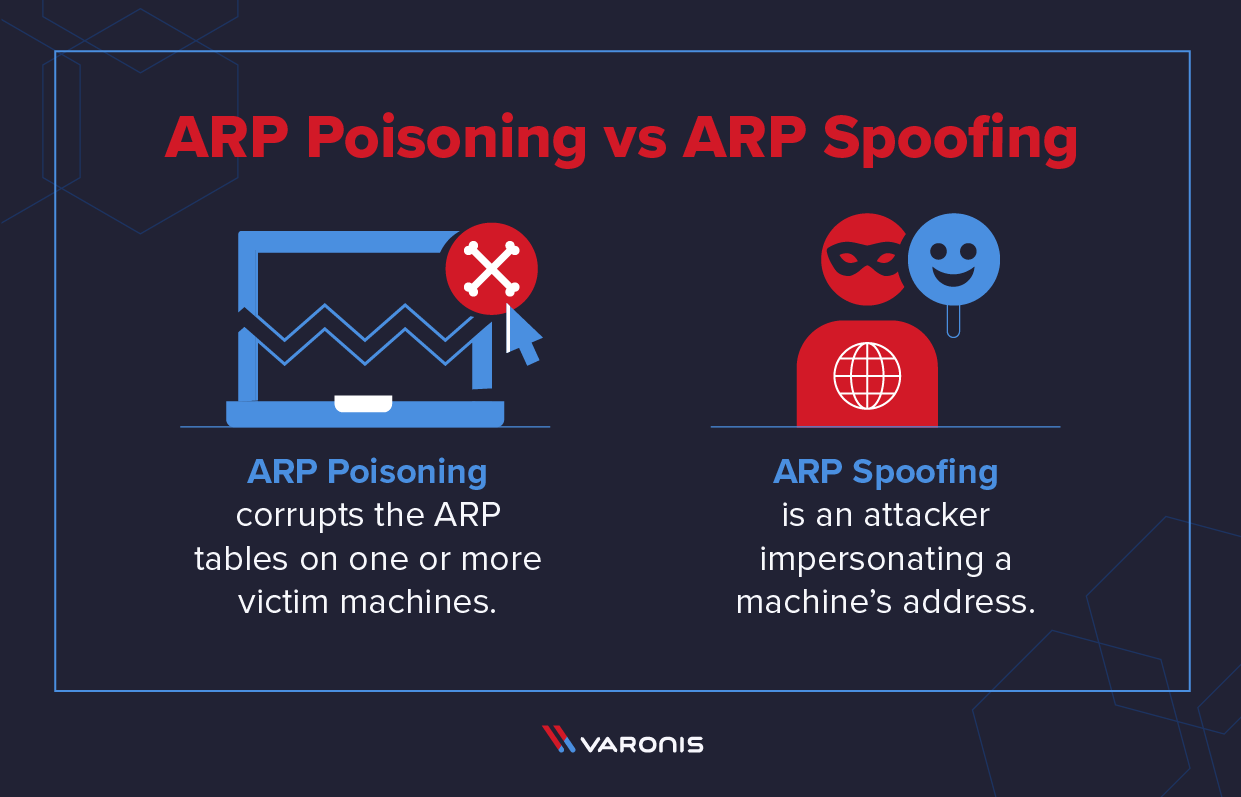
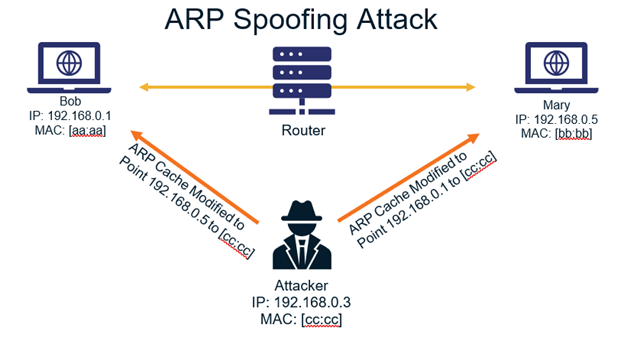
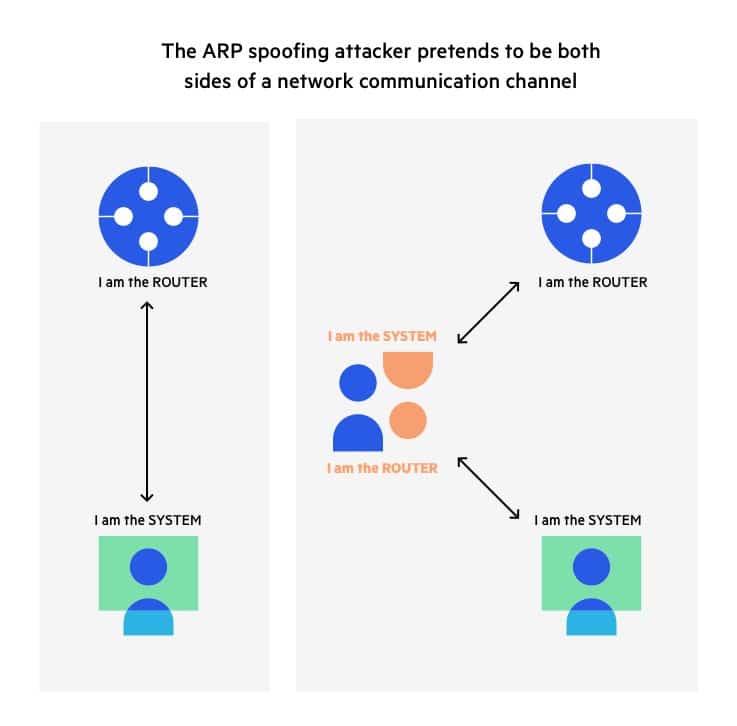
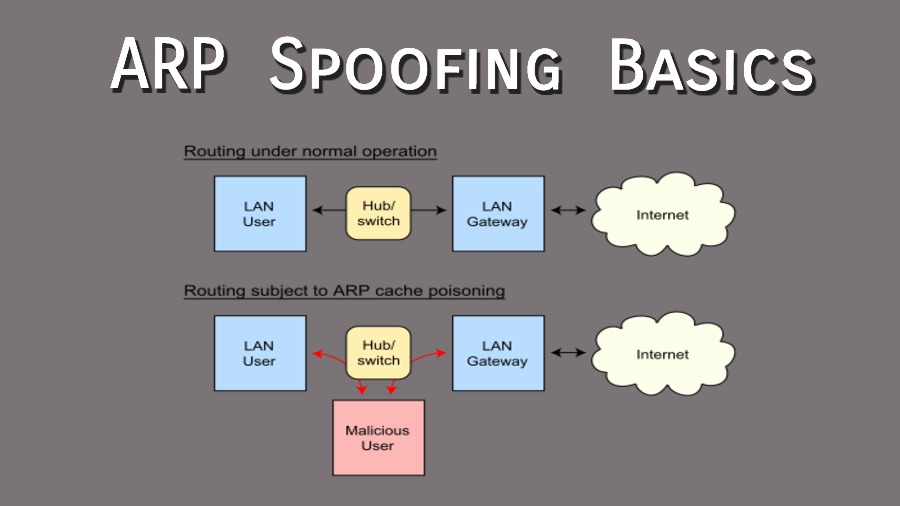
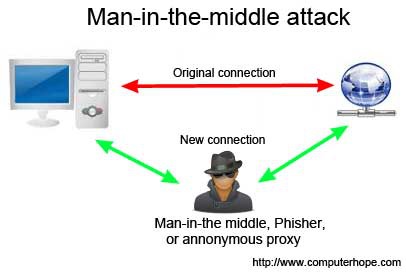
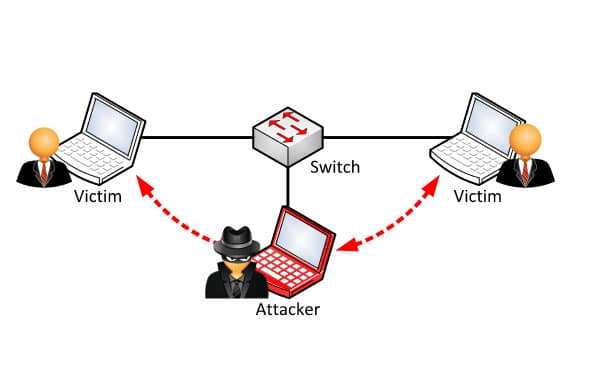
How to detect arp spoofing. The real mac address of the sender (we can easily get it by initiating an arp. Moving back to hometown covid x x This acts as a double.
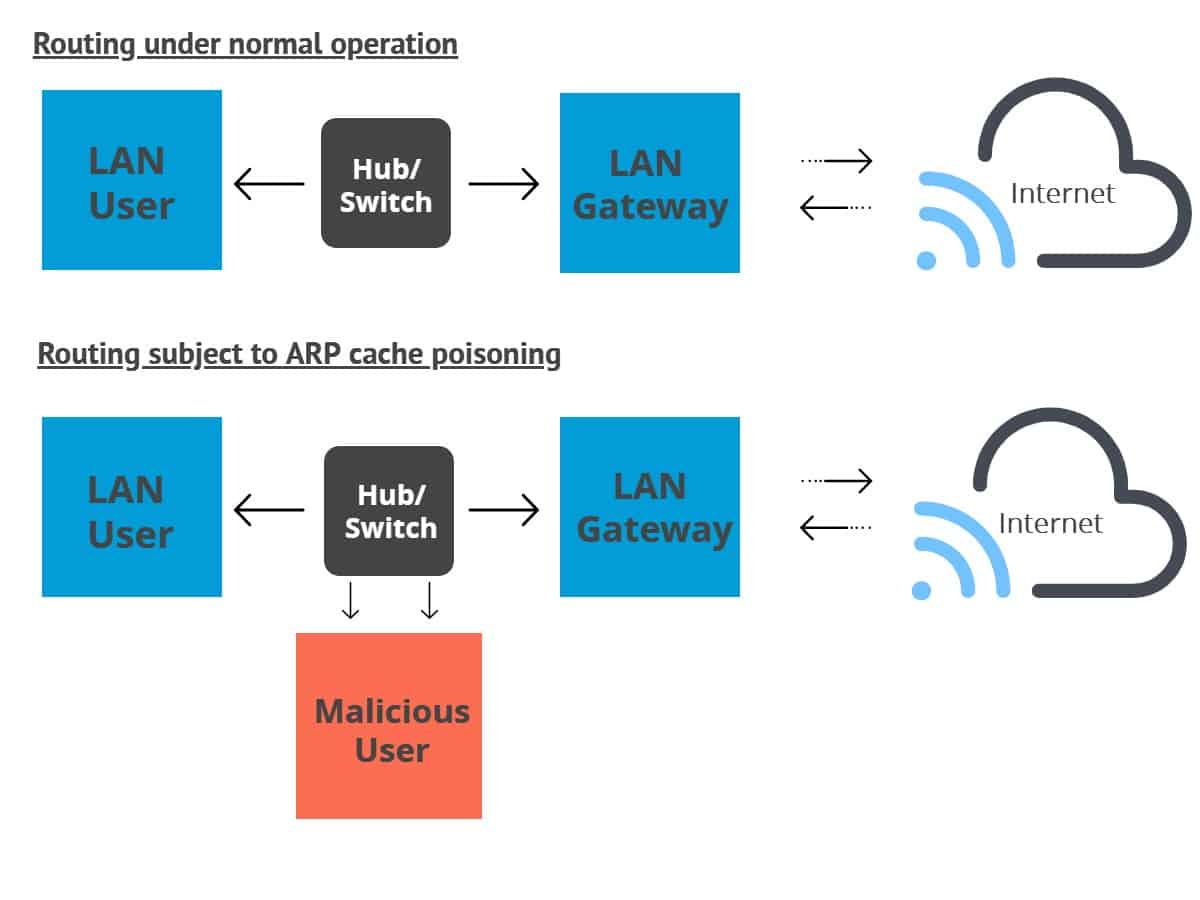
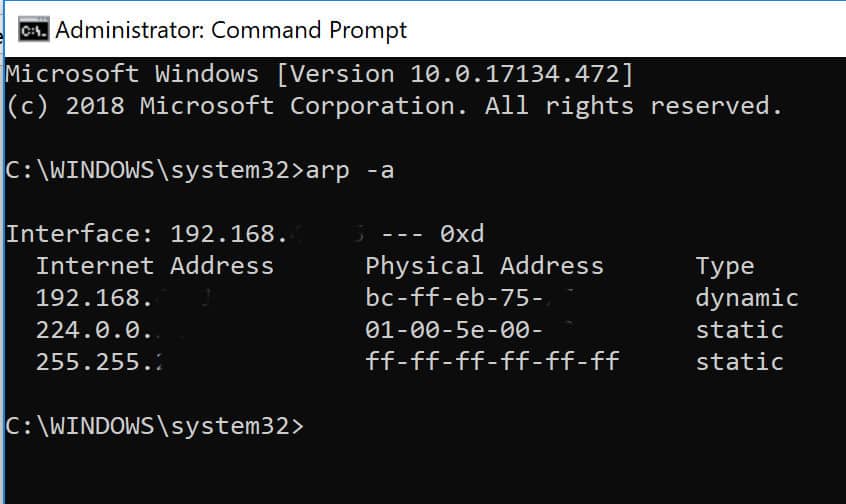
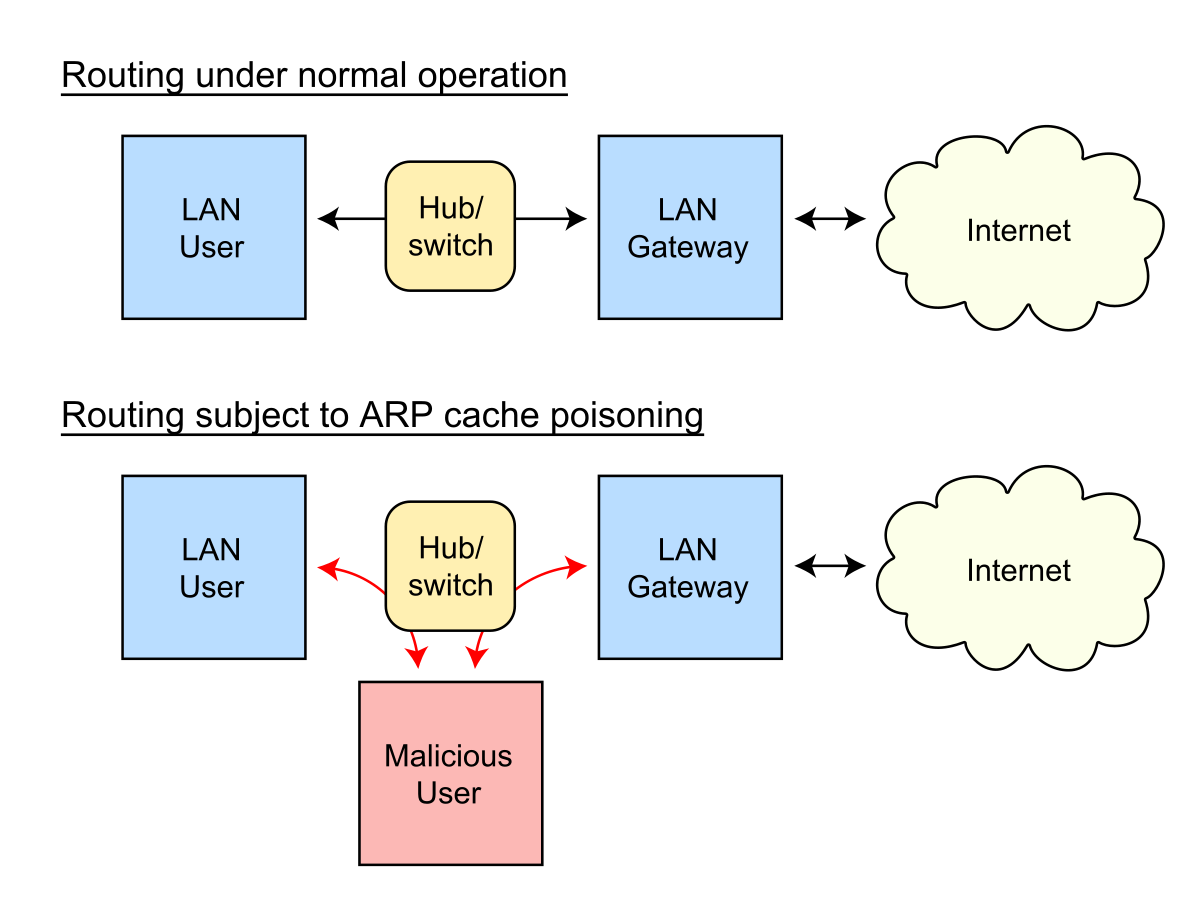
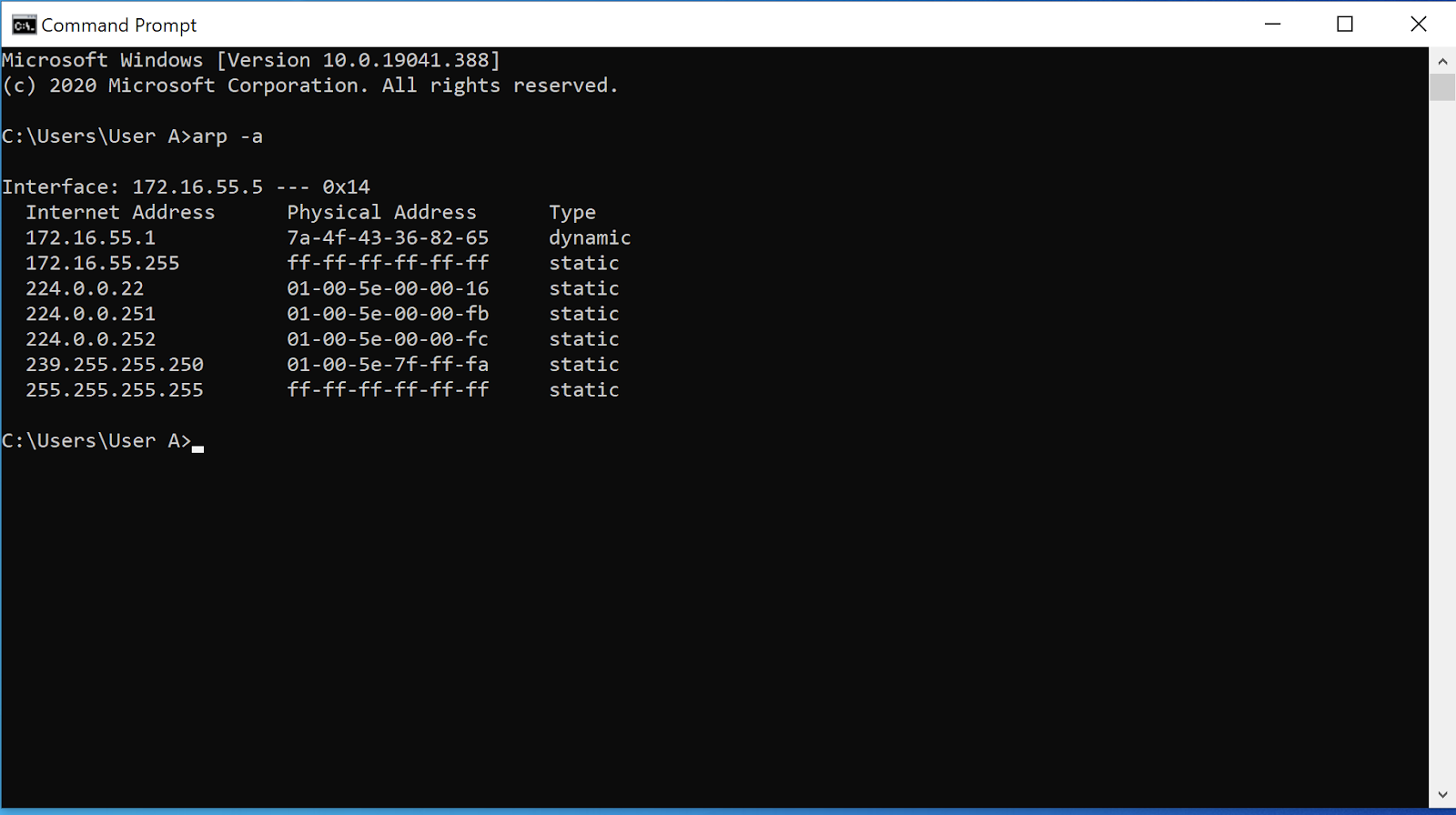
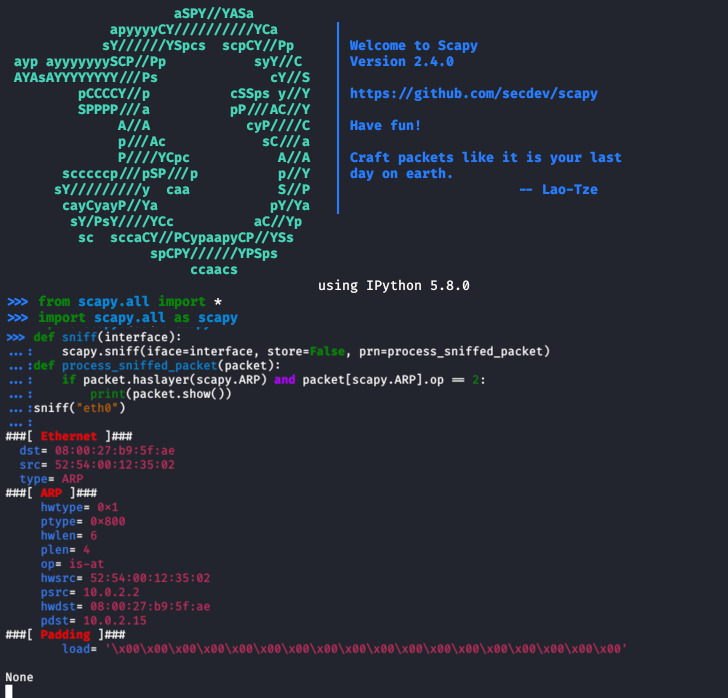
You can install it using: How can i protect myself against arp spoofing? Step 1 − first, when a machine wants to communicate with another it must look up to its arp table for physical address.
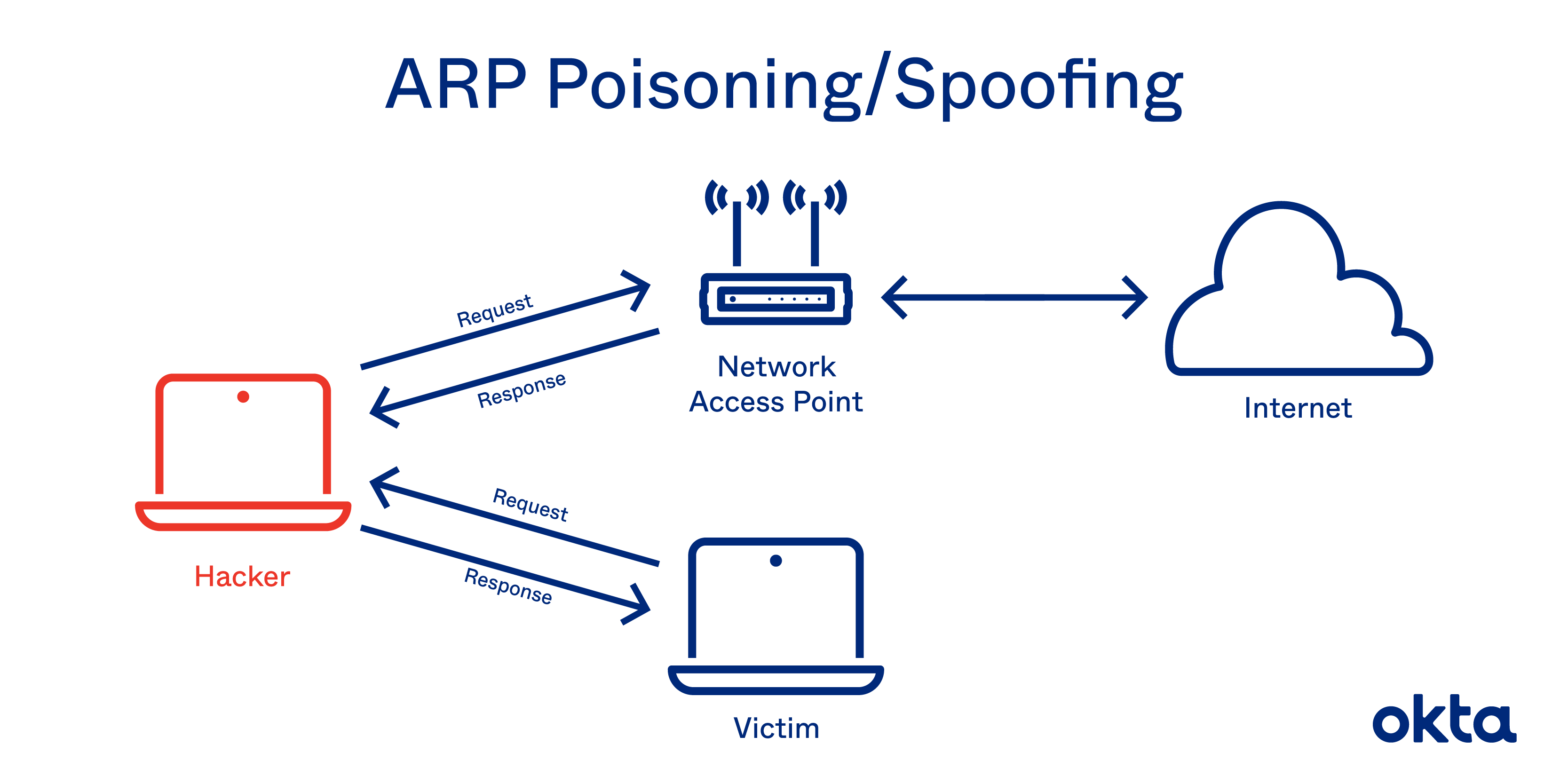
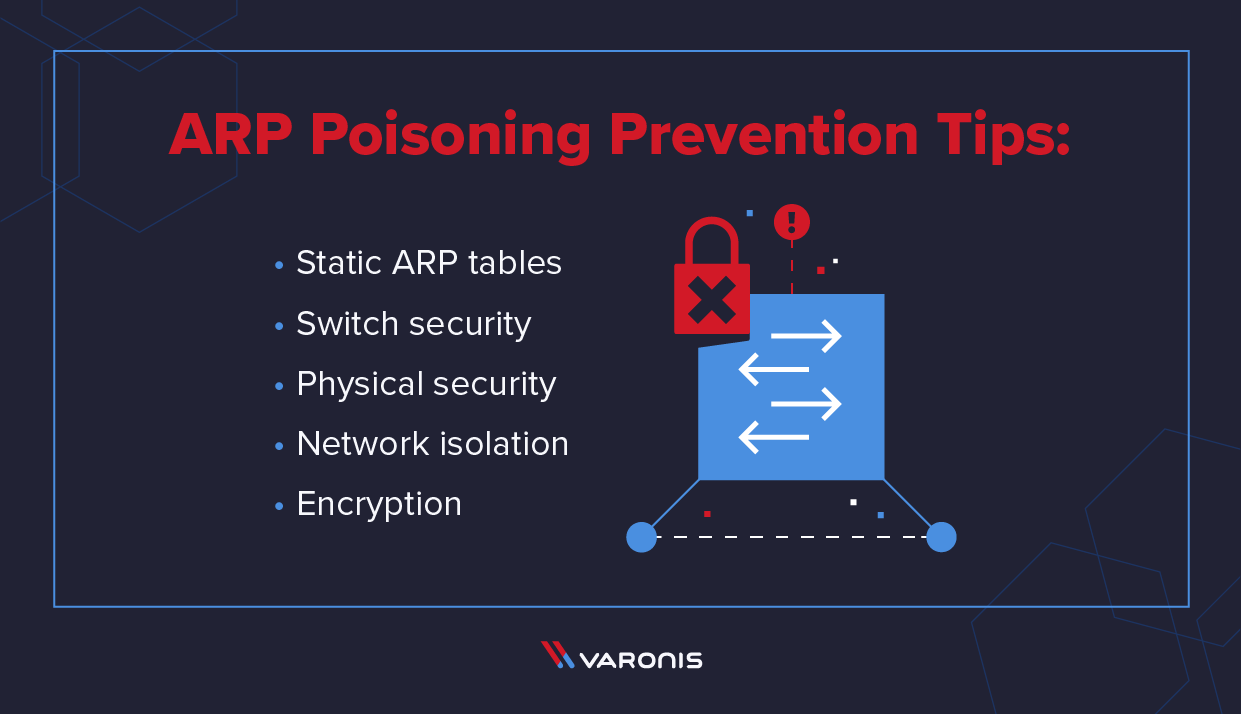
After python is installed on the terminal open the python shell and execute the command to install scapy, then to use scapy for arp spoof detection open scapy to write your. The attacker gains access to the local network and then scans it to find. There are several ways you can prevent arp spoofing attacks.
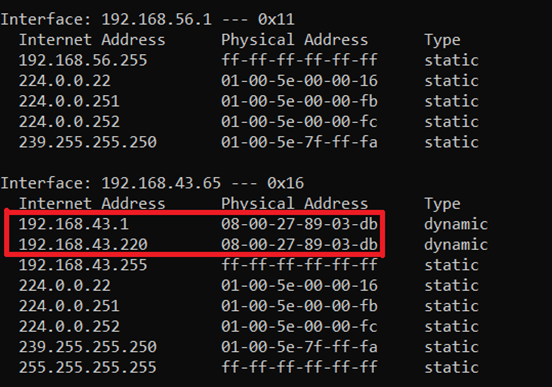
Change the contents of the file etter.dns, so the facebook.com points to your own ip. How to say meet in spanish pompadour hairstyle black female. The risk of being a victim of arp spoofing can be reduced by creating a static arp entry in the server.
This sometimes leads to the attack being discovered long after it has been. The other is to use a network protocol analyzer like wireshark. I am using debian linux.
How to tell if someone is spoofing your arp to tell if you’re being spoofed, check your task automation and configuration management program. The steps of an arp spoofing attack arp spoofing attacks usually follow the same general steps: The source mac address (that can be spoofed).